| Author
|
Post |
|
|
untanglingwebs
El Supremo
|
Obama Strikes Back at Russia for Election Hacking
By DAVID E. SANGERDEC. 29, 2016
WASHINGTON President Obama struck back at Russia on Thursday for its efforts to influence the 2016 election, ejecting 35 suspected Russian intelligence operatives from the United States and imposing sanctions on Russias two leading intelligence services.
The administration also penalized four top officers of one of those services, the powerful military intelligence unit known as the G.R.U.
Intelligence agencies have concluded that the G.R.U. ordered the attacks on the Democratic National Committee and other political organizations, with the approval of the Kremlin, and ultimately enabled the publication of the emails it harvested to benefit Donald J. Trumps campaign.
The expulsion of the 35 Russians, whom the administration said were spies posing as diplomats and other officials, and their families was in response to the harassment of American diplomats in Russia, State Department officials said. It was unclear if they were involved in the hacking.
In addition, the State Department announced the closing of two waterfront estates one in Glen Cove, N.Y., and another on Marylands Eastern Shore that it said were used for Russian intelligence activities, although officials declined to say whether they were specifically used in the election-related hacks.
Taken together, the sweeping actions announced by the White House, the Treasury, the State Department and intelligence agencies on Thursday amount to the strongest American response yet to a state-sponsored cyberattack. They also appeared intended to box in President-elect Trump, who will now have to decide whether to lift the sanctions on Russian intelligence agencies when he takes office next month.
Mr. Trump responded to the Russian sanctions late Thursday by reiterating a call to move on. But he pledged to meet with intelligence officials, who have concluded that the Russian hacking was an attempt to tip the election to Mr. Trump.
"Nothing to see here folks, move along." Putin and his wealthy friends have Trump in a money crunch. Like Deep Throat said in Watergate,...
In an earlier statement from Hawaii, Mr. Obama took a subtle dig at Mr. Trump, who has consistently cast doubt on the intelligence showing that the Russian government was deeply involved in the hacking. All Americans should be alarmed by Russias actions, Mr. Obama said, and added that the United States acted after repeated private and public warnings that we have issued to the Russian government, and are a necessary and appropriate response to efforts to harm U.S. interests in violation of established international norms of behavior.
He issued a new executive order that allows him, and his successors, to retaliate for efforts to influence elections in the United States or those of allies and partners, a clear reference to concern that Russias next target may be Germany and France. Already there are reports of influence operations in both.
Mr. Trumps position is at odds with most members of his party, who after classified briefings have called for investigations into the combination of cyberattacks and old-style information warfare used in the 2016 campaign. Mr. Trump has largely stuck to the theory he set forth in a debate with Hillary Clinton in September, when he said the hacks could have been organized by somebody sitting on their bed that weighs 400 pounds.
Russia criticized the sanctions and vowed retaliation.
Such steps of the U.S. administration that has three weeks left to work are aimed at two things: to further harm Russian-American ties, which are at a low point as it is, as well as, obviously, deal a blow on the foreign policy plans of the incoming administration of the president-elect, Dmitri S. Peskov, the spokesman for President Vladimir V. Putin, told reporters.
Konstantin Kosachyov, the head of the foreign affairs committee in the upper house of the Russian Parliament, told Interfax that this is the agony not even of lame ducks, but of political corpses.
Document
Report on Russian Hacking
The F.B.I. and Department of Homeland Security released a report on Thursday detailing the ways that Russia acted to influence the American election through cyberespionage.
OPEN Document
Despite the international fallout and political repercussions surrounding the announcement, it is not clear how much effect the sanctions will have, except on the ousted diplomats, who have until midday Sunday to leave the country. G.R.U. officials rarely travel to the United States, or keep assets here.
The four Russian intelligence officials are Igor Valentinovich Korobov, the chief of the G.R.U., and three deputies: Sergey Aleksandrovich Gizunov, Igor Olegovich Kostyukov and Vladimir Stepanovich Alexseyev.
Photo
President-elect Donald J. Trump responded to the Russian sanctions late Thursday by reiterating a call to move on. Credit Kevin Hagen for The New York Times
The administration also put sanctions on three companies and organizations that it said supported the hacking operations: the Special Technology Center, a signals intelligence operation in St. Petersburg, Russia; a firm called Zorsecurity that is also known as Esage Lab; and the Autonomous Noncommercial Organization Professional Association of Designers of Data Processing Systems, whose lengthy name, American officials said, was cover for a group that provided special training for the hacking.
Still, the sanctions go well beyond the modest sanctions imposed against North Korea for its attack on Sony Pictures Entertainment two years ago, which Mr. Obama said at the time was an effort to repress free speech a somewhat crude comedy, called The Interview, imagining a C.I.A. plot to assassinate Kim Jung-un, the countrys leader.
The Perfect Weapon: How Russian Cyberpower Invaded the U.S.
A Times investigation reveals missed signals, slow responses and a continuing underestimation of the seriousness of a campaign to disrupt the 2016 presidential election.
The sanctions are not as biting as previous ones in which the United States and its Western allies took aim at broad sectors of the Russian economy and blacklisted dozens of people, some of them close friends of Mr. Putins. Those sanctions were in response to the Russian annexation of Crimea and its activities to destabilize Ukraine. Mr. Trump suggested in an interview with The New York Times this year that he believed those sanctions were useless, and left open the possibility he might lift them.
The F.B.I. and the Department of Homeland Security on Thursday also released samples of malware and other indicators of Russian cyberactivity, including network addresses of computers commonly used by the Russians to start attacks. But the evidence in a report, in which the administration referred to the Russian cyberactivity as Grizzly Steppe, fell short of anything that would directly tie senior officers of the G.R.U. or the F.S.B., the other intelligence service, to a plan to influence the election.
Graphic: Following the Links From Russian Hackers to the U.S. Election
A more detailed report on the intelligence, ordered by Mr. Obama, will be published in the next three weeks, though much of the information especially evidence collected from implants in Russian computer systems, tapped conversations and spies is expected to remain classified.
Several Obama administration officials, including Vice President Joseph R. Biden Jr., have suggested that there may also be a covert response, one that would be obvious to Mr. Putin but not to the public.
Got a confidential news tip?
The New York Times would like to hear from readers who want to share messages and materials with our journalists.
While that may prove satisfying, many outside experts have said that unless the public response is strong enough to impose a real cost on Mr. Putin, his government and his vast intelligence apparatus, it might not deter further activity.
They are concerned about controlling retaliation, said James A. Lewis, a cyberexpert at the Center for Strategic and International Studies in Washington.
But John P. Carlin, who recently left the administration as the chief of the Justice Departments national security division, where he assembled cases against North Korean, Chinese and Iranian hackers, called the administrations actions a significant step that is consistent with a new model: When you violate norms of behavior in this space, we can figure out who did it and we can impose consequences.
The Obama administration was riven for months by an internal debate about how much of its evidence to make public. In interviews for a New York Times investigation into the hack, several of Mr. Obamas top aides expressed regret that they had not made evidence public earlier, or reacted more strongly. None said they believed it would have affected the outcome of the election, however.
In recent weeks, Mr. Obama decided that the authorities he created in April 2015 to retaliate against states or individuals that conduct hacking after the Sony attack did not go far enough. They made no provision issuing sanctions in response to an incursion on the electoral system an attack few saw coming.
So he ordered his lawyers to amend the executive order, specifically giving himself and his successor the authority to issue travel bans and asset freezes on those who tamper with, alter, or cause a misappropriation of information, with a purpose or effect of interfering with or undermining election processes or institutions.
The administration has not publicly criticized how its own officials handled the case. But the Times investigation revealed that the F.B.I. first informed the Democratic National Committee that it saw evidence that the committees email systems had been hacked in the fall of 2015. Months of fumbling and slow responses followed.
Mr. Obama said at a news conference that he was first notified early this summer. But one of his top aides met Russian officials in Geneva to complain about activity in April.
By the time the leadership of the committee woke up to what was happening, the G.R.U. had not only obtained emails through a hacking group that has been closely associated with it for years, but, investigators say, also allowed them to be published on a number of websites, including a newly created one called DC Leaks and the far more established WikiLeaks. Meanwhile, several states reported the scanning of their voter databases which American intelligence agencies also attributed to Russian hackers. But there is no evidence, American officials said, that Russia sought to manipulate votes or voter rolls on Nov. 8.
Mr. Obama decided not to issue sanctions earlier for fear of Russian retaliation ahead of Election Day. Some of his aides now believe that was a mistake. But the president made clear before leaving for Hawaii that he planned to respond.
Follow David E. Sanger on Twitter @SangerNYT.
Neil MacFarquhar contributed reporting from Moscow.
Last edited by untanglingwebs on Sat Dec 31, 2016 6:27 am; edited 1 time in total |
|
|
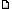 Fri Dec 30, 2016 5:45 am
Fri Dec 30, 2016 5:45 am |
|
|
untanglingwebs
El Supremo
|
Europe
How Russia Recruited Elite Hackers for Its Cyberwar
By ANDREW E. KRAMERDEC. 29, 2016
An internet security firm in Moscow. While much about Russias cyberwarfare program is shrouded in secrecy, details of the governments effort to recruit programmers in the months before the American presidential election shed light on the Kremlins plan to create teams of computer hackers. Credit Kirill
MOSCOW Aleksandr B. Vyarya thought his job was to defend people from cyberattacks until, he says, his government approached him with a request to do the opposite.
Mr. Vyarya, 33, a bearded, bespectacled computer programmer who thwarted hackers, said he was suddenly being asked to join a sweeping overhaul of the Russian military last year. Under a new doctrine, the nations generals were redefining war as more than a contest of steel and gunpowder, making cyberwarfare a central tenet in expanding the Kremlins interests.
Sorry, I cant, Mr. Vyarya said he told an executive at a Russian military contracting firm who had offered him the hacking job. But Mr. Vyarya was worried about the consequences of his refusal, so he abruptly fled to Finland last year, he and his former employer said. It was a rare example of a Russian who sought asylum in the face of the countrys push to recruit hackers.
This is against my principles and illegal, he said of the Russian militarys hacking effort.
While much about Russias cyberwarfare program is shrouded in secrecy, details of the governments effort to recruit programmers in recent years whether professionals like Mr. Vyarya, college students, or even criminals are shedding some light on the Kremlins plan to create elite teams of computer hackers.
American intelligence agencies say that a team of Russian hackers stole data from the Democratic National Committee during the presidential campaign. On Thursday, the Obama administration imposed sanctions against Russia for interfering in the election, the bedrock of the American political system.
The sanctions take aim at Russias main intelligence agencies and specific individuals, striking at one part of a sprawling cyberespionage operation that also includes the military, military contractors and teams of civilian recruits.
For more than three years, rather than rely on military officers working out of isolated bunkers, Russian government recruiters have scouted a wide range of programmers, placing prominent ads on social media sites, offering jobs to college students and professional coders, and even speaking openly about looking in Russias criminal underworld for potential talent.
Those recruits were intended to cycle through military contracting companies and newly formed units called science squadrons established on military bases around the country.
As early as 2013, Sergei K. Shoigu, the Russian defense minister, told university rectors at a meeting in Moscow that he was on a head hunt in the positive meaning of the word for coders.
Photo
Gen. Valery V. Gerasimov, the first deputy defense minister of Russia, with Foreign Minister Sergey V. Lavrov, right, in October. Mr. Gerasimov published the Gerasimov Doctrine, which said the lines between war and peace had blurred and that covert tactics like cyberwarfare would become most important. Credit Ozan Kose/Agence France-Presse Getty Images
The Defense Ministry bought advertising on Vkontakte, Russias most popular social network. One video shows a man clanging a military rifle on a table beside a laptop computer, then starting to type.
If you graduated from college, if you are a technical specialist, if you are ready to use your knowledge, we give you an opportunity, the ad intoned. Members of the science squadrons, the video said, live in comfortable accommodation, shown as an apartment furnished with a washing machine.
University students subject to mandatory conscription in the nations armed forces, but who wanted to avoid brutal stints as enlistees, could opt instead to join a science squadron. A government questionnaire asks draftees about their knowledge of programming languages.
The ministry posted openings on job forums, according to an investigation by Meduza, a Russian news site based in Riga, Latvia, that first disclosed the recruitment effort. One post from 2014 advertised for a computer scientist with knowledge of patches, vulnerabilities and exploits, which refers to sabotage used to alter a computer.
Given the size of Russias cybercrime underworld, it was not long before the military considered recruiting those it described as hackers who have problems with the law.
In an article titled Enlisted Hacker in Rossiiskaya Gazeta, the government newspaper, a deputy minister of defense, Gen. Oleg Ostapenko, said the science squadrons might include hackers with criminal histories. From the point of view of using scientific potential, this is a matter for discussion, he was quoted as saying in 2013.
Experts say the strategy was more than just talk.
There have been cases where cybercriminals are arrested but never ended up in prison, said Dmitri Alperovitch, the co-founder and chief technology officer of CrowdStrike, the cybersecurity company that first identified the group known as Fancy Bear as the perpetrator of the Democratic National Committee hacking.
Mr. Vyarya, the programmer who turned down the governments job offer, was an attractive recruit from the opposite end of the spectrum: someone with a career protecting people against hackers.
Specifically, he had experience shielding websites from a maneuver called a distributed denial of service, or DDoS attack, in which the sites are overwhelmed and disabled by a torrent of fake traffic. Among his clients were Vedomosti, an independent newspaper; TV Rain, an opposition-leaning television station; and the website of Aleksei A. Navalny, the opposition leader.
Mr. Vyarya said that in 2015 he was invited to accompany Vasily Brovko, an executive at the military contracting company Rostec, on a trip to Sofia, Bulgaria. But he said it turned out to be a demonstration of a new software suite capable of staging DDoS attacks.
Photo
Dmitry A. Artimovich, a physicist who designed a computer program that emailed male sexual enhancement spam, in Moscow. He decided not to volunteer for a cyberwarfare unit to avoid a prison term. Credit James Hill for The New York Times
The Bulgarian firm demonstrating the software briefly crashed the website of Ukraines Defense Ministry and Slon.ru, a Russian news website, Mr. Vyarya said. Slon.ru has confirmed its site went down inexplicably for about two minutes that day, Feb. 5, 2015.
After the demonstration, Mr. Vyarya said Mr. Brovko asked him how the program might be improved. Then, according to Mr. Vyarya, Mr. Brovko offered him a job running the DDoS software, which he said the Russians planned to buy from the Bulgarians for about $1 million.
Mr. Vyarya said his problems began when he turned down the offer: He was surveilled, and an acquaintance in law enforcement advised him to flee the country. He left in August 2015 for Finland to seek asylum, he and his former employer said. The Finnish government, citing safety and privacy concerns, would not comment on the asylum application.
As soon as we saw what was on the table, Sasha was given direct instructions to return to his hotel and stop all contacts, said his former boss, Aleksandr V. Lyamin of Qrator, a cyberdefense company in Moscow, using Mr. Vyaryas Russian nickname. But the overtures from the military contractor persisted, Mr. Lyamin said, and Mr. Vyarya fled.
Rostec strongly denied Mr. Vyaryas account. Mr. Brovko did travel to Bulgaria with Mr. Vyarya, the company said, but to evaluate software for defensive, not offensive, cybersystems. A spokeswoman for Mr. Brovko called the account of crashing sites in a product demonstration the imagination of a mentally unstable man.
The militarys push into cyberwarfare had intensified in 2012, with the appointment of a new minister of defense, Mr. Shoigu. The next year, a senior defense official, Gen. Valery V. Gerasimov published what became known as the Gerasimov Doctrine. It posited that in the world today, the lines between war and peace had blurred and that covert tactics, such as working through proxies or otherwise in the shadows, would rise in importance.
He called it nonlinear war. His critics called it guerrilla geopolitics.
But Russia is certainly not alone.
Almost all developed countries in the world, unfortunately, are creating offensive capabilities, and many have confirmed this, said Anton M. Shingarev, a vice president at Kaspersky, a Russian antivirus company.
Recruitment by Russias military should be expected, he said. You or I might be angry about it, but, unfortunately, its just reality. Many countries are doing it. This is the reality.
American intelligence agencies, including the National Security Agency, have for decades recruited on college campuses. In 2015, the N.S.A. offered a free summer camp to 1,400 high school and middle school students, where they were taught the basics of hacking, cracking and cyberdefense.
Russia's Dark Arts
In Russia, recruiters have looked well beyond the nations school system.
In 2013, as Russias recruitment drive was picking up, Dmitry A. Artimovich, a soft-spoken physicist, was awaiting trial in a Moscow jail for designing a computer program that spammed email users with advertisements for male sexual enhancement products.
One day a cellmate, who had been convicted of selling narcotics online, sidled up to him with some news. The cellmate said that people incarcerated for cybercrimes could get out before trial, in exchange for working for the government. Another inmate had already taken a deal, he said.
It was an offer to cooperate, Mr. Artimovich said.
Why else would you work for the government? he added. The salaries are tiny. But if you do something illegal, and go to prison for eight or nine years, the F.S.B. can help you, he said, using a Russian abbreviation for the Federal Security Service.
Mr. Artimovich said he decided to take his chances at trial, and served a year in a penal colony.
As Russia ramped up its abilities, government agencies were also in the market for surveillance and hacking software, including some from legal suppliers in the West.
In 2014, a Russian company called Advanced Monitoring that has a license to work with the F.S.B., the agency that succeeded the K.G.B. after the fall of the Soviet Union, bought iPhone hacking software from an Italian company called Hacking Team, according to invoices published by WikiLeaks. Hacking Team has since lost its export license.
Western cybersecurity analysts believe they have identified the one responsible for the breaching the Democratic National Committee: a group nicknamed Fancy Bear.
First known as Advanced Persistent Threat 28, the group has been active since 2007 but its abilities evolved to emphasize attacks, rather than gather intelligence, after the military placed a priority on cyberwarfare.
It stepped up faketivist actions that released stolen data through contrived online personalities like Guccifer 2 and websites like DCLeaks, according to Kyle Ehmke, a senior intelligence researcher at ThreatConnect, a cybersecurity company. The group had been called Pawn Storm, named for a chess maneuver. It was nicknamed Fancy Bear in 2014.
This year, the group appropriated the nickname for its own use, setting up the website fancybear.net and publishing hacked data from the World Anti-Doping Agency, which showed that many American athletes, including the American tennis star Serena Williams, had medical exemptions to take banned substances. The hacking was apparently in retaliation for revelations of Russian doping in sports.
President Vladimir V. Putin has said repeatedly, most recently at his annual year-end news conference, that the information released in the recent hacking of the Democratic National Committee was more important than who was behind them.
The main thing, to my mind, is the information the hackers provided, Mr. Putin said of this summers cyberattack.
Democratic Party members and the Obama administration should not look abroad for someone to blame for losing the election, Mr. Putin said. You need to learn how to lose gracefully, he said.
Follow Andrew E. Kramer on Twitter @AndrewKramerNYT. |
|
|
 Fri Dec 30, 2016 6:19 am
Fri Dec 30, 2016 6:19 am |
|
|
untanglingwebs
El Supremo
|
How We Identified the D.N.C. Hacks Patient Zero
By ERIC LIPTONDEC. 20, 2016
Times Insider delivers behind-the-scenes insights into how news, features and opinion come together at The New York Times. In this article, the Pulitzer Prize-winning investigative reporter Eric Lipton details how he and his Times colleagues David E. Sanger and Scott Shane constructed a chronological narrative of one of the most famous hacks in history.
Epidemiologists, at the outbreak of any major disease, are sent out to the field to find patient zero the first victim, which helps explain how the contagion began. As David Sanger, Scott Shane and I set out in late November to reconstruct the events surrounding the hacking of the Democratic Party during the 2016 election campaign, we too wanted to understand, among all factors, how and where this story started.
The Times had extensively covered the remarkable story of Russias effort to influence the election with David Sanger and our colleague Eric Schmitt first breaking the news back in late July that the hack was almost certainly the work of Russian operatives (after David and Nicole Perlroth had explored how the Russians were casting the Democratic convention into chaos). That was followed in August with an article about suspicions that the N.S.A. itself was hacked by the Russians and in October with analysis of President Obamas options for retaliation.
But we had never taken the opportunity to look back and tell the story as a single, extended narrative, chronicling the people who got swept into one of the most famous hacks in history. Kitty Bennett, our news researcher extraordinaire, helped start the effort by building a chronology of events based on as many primary source documents as we could find.
The Perfect Weapon: How Russian Cyberpower Invaded the U.S.
A Times investigation reveals missed signals, slow responses and a continuing underestimation of the seriousness of a campaign to disrupt the 2016 presidential election.
We then set out to interview every major figure involved in the episode: the executives and staffers at the Democratic National Committee, the Democratic Congressional Campaign Committee and Hillary Clintons campaign; the private sector investigator at CrowdStrike, a cybersecurity firm, and Perkins Coie, a law firm, both of which were hired by the D.N.C. and the D.C.C.C.; the government investigators from the Federal Bureau of Investigation, the director of National Intelligence and the White House officials who advised President Obama on how to respond. We talked to members of Congress and other congressional candidates, and to intelligence officials who, of course, would not speak on the record. And that was just the beginning.
We also reached out to WikiLeaks and its editor in chief, Julian Assange and tried, though without much success, to engage individuals in the Russian government, as well as Guccifer 2.0 and DCLeaks, the Russian-linked websites that dumped many of the Democrats emails and other documents.
In each of these interviews, we asked the principal players not only to tell their stories, from start to finish, but also to provide us with primary source documents, such as emails or memos, even if they shared them on the condition that we could not reproduce them. Documents are better than human memory: They nail down names and days and times some of the last captured emails offered windows into how various email accounts were cracked open and sometimes give us a sense of contemporaneous reactions. The Democratic Party officials were surprisingly open to telling this story, as they almost all felt that the media had focused far too much on the content of the stolen emails themselves and not nearly enough on how the 2016 election had been disrupted by a Russian plot. The White House didnt want to discuss the topic.
Kitty Bennetts original chronology grew in length, as we filled it in based on our interviews and collected documents, ultimately reaching more than 10,000 words: a 28-page compilation of people and events that served as the core of our narrative.
It was while doing all these interviews that we first heard the story of Yared Tamene, the tech-services consultant at the D.N.C. who had fielded a call in September 2015 from an F.B.I. special agent named Adrian Hawkins who contacted the D.N.C. to disclose that federal officials had evidence that the D.N.C. computer system had already been hacked. But Mr. Tamene did not believe he was talking to a real F.B.I. agent, so he didnt move definitively to find and shut down this intrusion.
Even after Special Agent Hawkins repeatedly called Mr. Tamene and finally met with him in person last January, he remained skeptical, describing their encounter this way in an internal D.N.C. memo: During this meeting, SA Hawkins showed his FBI badge to us, and shared his business card, lending some credence to his claim about working for the FBI. This was five months after the F.B.I. had first contacted the D.N.C. But Special Agent Hawkinss superiors took no steps to independently reach out to the committees leaders to persuade them to take seriously what appeared to be a Russian government attack. Between the passivity of the F.B.I. and the passivity of the D.N.C., almost no progress had been made to identify and lock out the hackers.
Mr. Tamene never agreed to speak with us, although we happened to run into him during one of our visits to D.N.C. headquarters. But based on documents we reviewed including an internal D.N.C. account of his dealings with the F.B.I. that Mr. Tamene himself had written we were confident we had found our patient zero. Our story would start in September 2015, when this first warning call had come in from the FBI.
When you do reporting like this, you begin to hear the same stories over and over again, told by different players who experienced the same events. These accounts might seem redundant. But for reporters, theyre vital stuff, because each person fills in different tidbits or pieces of color, as we call them. These overlapping stories help increase your confidence that the version of events youre piecing together is fair and true, particularly when backed up with emails and other documents.
While I was focused on the D.N.C., David was busy pressing Obama administration officials to explain how they responded to the cyberattacks a time-consuming process because of the difficulty of getting access to them and, in some cases, because of their reluctance to talk. David is perhaps the best-sourced cybersecurity reporter in the United States: He was the guy who broke the story of the most sophisticated cyberattack in history, the American-Israeli attack on Irans nuclear facilities. (That tale recently became a documentary.) Eventually the White House began to tell its story, and its no surprise that when President Obama gave his news conference on Friday, his version of events echoed what we had already reported.
While David worked, Scott Shane, one of the top intelligence reporters in Washington, focused on the F.B.I. and on a group we called the facilitators, which included players like WikiLeaks that posted the hacked emails in a public place. He also spent a large chunk of time examining the evidence investigators had gathered as proof that the Russian state was involved in the hack we went into this project determined to evaluate it on our own rather than base our work on an assumption that this was Russian espionage.
What is often most fascinating when you do so-called narrative reconstructs like this is how seemingly minor events can in retrospect have such enormous consequences. Consider the case of Charles Delavan, an aide to Hillary Clintons campaign, who in March 2016 was forwarded the phishing email that had been sent to John D. Podesta, the chairman of the Clinton campaign. Mr. Delavan had been asked to advise Mr. Podesta if this was a real email from Google, asking him to change the password on his personal Gmail account, or a hoax, trying to hack into Mr. Podestas account.
The Clinton campaign, simultaneously, was the target of an aggressive cyberattack that relied in large part on near replicas of this same fake Google email, urging recipients to change their password. So Mr. Delavan, in an interview, said he immediately knew this was a fake. And to me, as a reporter, that was a plausible statement.
But somehow and this action by Mr. Delavan remains inexplicable he wrote back that the fake Google email was legitimate, leading Mr. Podesta or one of his aides to fall for the ruse. This opened up to the Russian hackers a decades worth of Mr. Podestas emails (60,000 in total), including those that contained copies of speeches Mrs. Clinton had given on Wall Street, as well as hundreds of private exchanges he had had with other close aides. All of these became public, causing a distraction to Mrs. Clintons campaign in its critical final month.
The mistake, Mr. Delavan said in the interview, is the worst thing that ever happened in my life. He has become a target of threats via Twitter, email and telephone, with one person even coming to his house in Brooklyn before the election to tell him, You are going to make us lose the election. It is a burden he will carry with him for the rest of his life.
As we moved toward wrapping up our reporting, the history almost overtook us.
During one of these weekends, I happened to be at Politics and Prose, a popular Washington bookstore, interviewing a former D.N.C. staffer. At the same time, a gunman entered Comet Ping Pong, a pizza restaurant a few doors down, and fired his weapon. He was there to check out a fictional story suggesting that this pizza place was somehow the center of a child-trafficking ring. This conspiracy had been inspired with no justification in reality by the same set of emails stolen from John Podesta. The narrative of the Russian hacks we were reporting had driven right into this bookstore coffee shop. I wondered as I continued the interview, with police officers in body armor holding rifles right outside the window, should I crouch down under the table or keep talking? (Ultimately, I called the weekend editor in our Washington Bureau and wrote a breaking news story on the incident.)
The doorstopper-size history books we read make it seem like much of what happens as the pages turn is a matter of fate. It all had to happen that way, right? My impression is quite different. History, as this story once again illustrates, is marked by a lot of happenstance small but consequential acts that ricochet out into the world, writing the narrative in real time as the events unfold. |
|
|
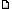 Fri Dec 30, 2016 6:33 am
Fri Dec 30, 2016 6:33 am |
|
|
untanglingwebs
El Supremo
|
The Perfect Weapon: How Russian Cyberpower Invaded the U.S.
Читать статью по-русски
By ERIC LIPTON, DAVID E. SANGER and SCOTT SHANEDEC. 13, 2016
WASHINGTON When Special Agent Adrian Hawkins of the Federal Bureau of Investigation called the Democratic National Committee in September 2015 to pass along some troubling news about its computer network, he was transferred, naturally, to the help desk.
His message was brief, if alarming. At least one computer system belonging to the D.N.C. had been compromised by hackers federal investigators had named the Dukes, a cyberespionage team linked to the Russian government.
The F.B.I. knew it well: The bureau had spent the last few years trying to kick the Dukes out of the unclassified email systems of the White House, the State Department and even the Joint Chiefs of Staff, one of the governments best-protected networks.
Yared Tamene, the tech-support contractor at the D.N.C. who fielded the call, was no expert in cyberattacks. His first moves were to check Google for the Dukes and conduct a cursory search of the D.N.C. computer system logs to look for hints of such a cyberintrusion. By his own account, he did not look too hard even after Special Agent Hawkins called back repeatedly over the next several weeks in part because he wasnt certain the caller was a real F.B.I. agent and not an impostor.
I had no way of differentiating the call I just received from a prank call, Mr. Tamene wrote in an internal memo, obtained by The New York Times, that detailed his contact with the F.B.I.
It was the cryptic first sign of a cyberespionage and information-warfare campaign devised to disrupt the 2016 presidential election, the first such attempt by a foreign power in American history. What started as an information-gathering operation, intelligence officials believe, ultimately morphed into an effort to harm one candidate, Hillary Clinton, and tip the election to her opponent, Donald J. Trump.
Like another famous American election scandal, it started with a break-in at the D.N.C. The first time, 44 years ago at the committees old offices in the Watergate complex, the burglars planted listening devices and jimmied a filing cabinet. This time, the burglary was conducted from afar, directed by the Kremlin, with spear-phishing emails and zeros and ones.
What is phishing?
Phishing uses an innocent-looking email to entice unwary recipients to click on a deceptive link, giving hackers access to their information or a network. In spear-phishing, the email is tailored to fool a specific person.
An examination by The Times of the Russian operation based on interviews with dozens of players targeted in the attack, intelligence officials who investigated it and Obama administration officials who deliberated over the best response reveals a series of missed signals, slow responses and a continuing underestimation of the seriousness of the cyberattack.
The D.N.C.s fumbling encounter with the F.B.I. meant the best chance to halt the Russian intrusion was lost. The failure to grasp the scope of the attacks undercut efforts to minimize their impact. And the White Houses reluctance to respond forcefully meant the Russians have not paid a heavy price for their actions, a decision that could prove critical in deterring future cyberattacks.
The low-key approach of the F.B.I. meant that Russian hackers could roam freely through the committees network for nearly seven months before top D.N.C. officials were alerted to the attack and hired cyberexperts to protect their systems. In the meantime, the hackers moved on to targets outside the D.N.C., including Mrs. Clintons campaign chairman, John D. Podesta, whose private email account was hacked months later.
Even Mr. Podesta, a savvy Washington insider who had written a 2014 report on cyberprivacy for President Obama, did not truly understand the gravity of the hacking.
By last summer, Democrats watched in helpless fury as their private emails and confidential documents appeared online day after day procured by Russian intelligence agents, posted on WikiLeaks and other websites, then eagerly reported on by the American media, including The Times. Mr. Trump gleefully cited many of the purloined emails on the campaign trail.
The fallout included the resignations of Representative Debbie Wasserman Schultz of Florida, the chairwoman of the D.N.C., and most of her top party aides. Leading Democrats were sidelined at the height of the campaign, silenced by revelations of embarrassing emails or consumed by the scramble to deal with the hacking. Though little-noticed by the public, confidential documents taken by the Russian hackers from the D.N.C.s sister organization, the Democratic Congressional Campaign Committee, turned up in congressional races in a dozen states, tainting some of them with accusations of scandal.
In recent days, a skeptical president-elect, the nations intelligence agencies and the two major parties have become embroiled in an extraordinary public dispute over what evidence exists that President Vladimir V. Putin of Russia moved beyond mere espionage to deliberately try to subvert American democracy and pick the winner of the presidential election.
Many of Mrs. Clintons closest aides believe that the Russian assault had a profound impact on the election, while conceding that other factors Mrs. Clintons weaknesses as a candidate; her private email server; the public statements of the F.B.I. director, James B. Comey, about her handling of classified information were also important.
While theres no way to be certain of the ultimate impact of the hack, this much is clear: A low-cost, high-impact weapon that Russia had test-fired in elections from Ukraine to Europe was trained on the United States, with devastating effectiveness. For Russia, with an enfeebled economy and a nuclear arsenal it cannot use short of all-out war, cyberpower proved the perfect weapon: cheap, hard to see coming, hard to trace.
The Obama administration announced sanctions against Russia and released a report that states that the Russian government deployed computer hackers to attack the Democratic Partys computers.
There shouldnt be any doubt in anybodys mind, Adm. Michael S. Rogers, the director of the National Security Agency and commander of United States Cyber Command, said at a postelection conference. This was not something that was done casually, this was not something that was done by chance, this was not a target that was selected purely arbitrarily, he said. This was a conscious effort by a nation-state to attempt to achieve a specific effect.
For the people whose emails were stolen, this new form of political sabotage has left a trail of shock and professional damage. Neera Tanden, president of the Center for American Progress and a key Clinton supporter, recalls walking into the busy Clinton transition offices, humiliated to see her face on television screens as pundits discussed a leaked email in which she had called Mrs. Clintons instincts suboptimal.
It was just a sucker punch to the gut every day, Ms. Tanden said. It was the worst professional experience of my life.
Theres no plausible
actor that has an
interest in all those
victims other than Russia.
DMITRI ALPEROVITCH, co-founder of CrowdStrike, a cybersecurity firm retained by the D.N.C.
The United States, too, has carried out cyberattacks, and in decades past the C.I.A. tried to subvert foreign elections. But the Russian attack is increasingly understood across the political spectrum as an ominous historic landmark with one notable exception: Mr. Trump has rejected the findings of the intelligence agencies he will soon oversee as ridiculous, insisting that the hacker may be American, or Chinese, but that they have no idea.
Mr. Trump cited the reported disagreements between the agencies about whether Mr. Putin intended to help elect him. On Tuesday, a Russian government spokesman echoed Mr. Trumps scorn.
This tale of hacks resembles a banal brawl between American security officials over spheres of influence, Maria Zakharova, the spokeswoman for the Russian Foreign Ministry, wrote on Facebook.
Democratic House Candidates Were Also Targets of Russian Hacking
The fallout for nearly a dozen congressional candidates underscores the effect of the Russian influence operation on the American electoral system.
Over the weekend, four prominent senators two Republicans and two Democrats joined forces to pledge an investigation while pointedly ignoring Mr. Trumps skeptical claims.
Democrats and Republicans must work together, and across the jurisdictional lines of the Congress, to examine these recent incidents thoroughly and devise comprehensive solutions to deter and defend against further cyberattacks, said Senators John McCain, Lindsey Graham, Chuck Schumer and Jack Reed.
This cannot become a partisan issue, they said. The stakes are too high for our country.
A Target for Break-Ins
Sitting in the basement of the Democratic National Committee headquarters, below a wall-size 2012 portrait of a smiling Barack Obama, is a 1960s-era filing cabinet missing the handle on the bottom drawer. Only a framed newspaper story hanging on the wall hints at the importance of this aged piece of office furniture.
GOP Security Aide Among 5 Arrested in Bugging Affair, reads the headline from the front page of The Washington Post on June 19, 1972, with the bylines of Bob Woodward and Carl Bernstein.
Andrew Brown, 37, the technology director at the D.N.C., was born after that famous break-in. But as he began to plan for this years election cycle, he was well aware that the D.N.C. could become a break-in target again.
There were aspirations to ensure that the D.N.C. was well protected against cyberintruders and then there was the reality, Mr. Brown and his bosses at the organization acknowledged: The D.N.C. was a nonprofit group, dependent on donations, with a fraction of the security budget that a corporation its size would have.
There was never enough money to do everything we needed to do, Mr. Brown said.
The D.N.C. had a standard email spam-filtering service, intended to block phishing attacks and malware created to resemble legitimate email. But when Russian hackers started in on the D.N.C., the committee did not have the most advanced systems in place to track suspicious traffic, internal D.N.C. memos show.
Mr. Tamene, who reports to Mr. Brown and fielded the call from the F.B.I. agent, was not a full-time D.N.C. employee; he works for a Chicago-based contracting firm called The MIS Department. He was left to figure out, largely on his own, how to respond and even whether the man who had called in to the D.N.C. switchboard was really an F.B.I. agent.
The F.B.I. thinks the D.N.C. has at least one compromised computer on its network and the F.B.I. wanted to know if the D.N.C. is aware, and if so, what the D.N.C. is doing about it, Mr. Tamene wrote in an internal memo about his contacts with the F.B.I. He added that the Special Agent told me to look for a specific type of malware dubbed Dukes by the U.S. intelligence community and in cybersecurity circles.
Part of the problem was that Special Agent Hawkins did not show up in person at the D.N.C. Nor could he email anyone there, as that risked alerting the hackers that the F.B.I. knew they were in the system.
Photo
An internal memo by Yared Tamene, a tech-support contractor at the D.N.C., expressed uncertainty about the identity of Special Agent Adrian Hawkins of the F.B.I., who called to inform him of the breach.
Mr. Tamenes initial scan of the D.N.C. system using his less-than-optimal tools and incomplete targeting information from the F.B.I. found nothing. So when Special Agent Hawkins called repeatedly in October, leaving voice mail messages for Mr. Tamene, urging him to call back, I did not return his calls, as I had nothing to report, Mr. Tamene explained in his memo.
In November, Special Agent Hawkins called with more ominous news. A D.N.C. computer was calling home, where home meant Russia, Mr. Tamenes memo says, referring to software sending information to Moscow. SA Hawkins added that the F.B.I. thinks that this calling home behavior could be the result of a state-sponsored attack.
Mr. Brown knew that Mr. Tamene, who declined to comment, was fielding calls from the F.B.I. But he was tied up on a different problem: evidence suggesting that the campaign of Senator Bernie Sanders of Vermont, Mrs. Clintons main Democratic opponent, had improperly gained access to her campaign data.
Ms. Wasserman Schultz, then the D.N.C.s chairwoman, and Amy Dacey, then its chief executive, said in interviews that neither of them was notified about the early reports that the committees system had likely been compromised.
Shawn Henry, who once led the F.B.I.s cyber division and is now president of CrowdStrike Services, the cybersecurity firm retained by the D.N.C. in April, said he was baffled that the F.B.I. did not call a more senior official at the D.N.C. or send an agent in person to the party headquarters to try to force a more vigorous response.
We are not talking about an office that is in the middle of the woods of Montana, Mr. Henry said. We are talking about an office that is half a mile from the F.B.I. office that is getting the notification.
This is not a mom-and-pop delicatessen or a local library. This is a critical piece of the U.S. infrastructure because it relates to our electoral process, our elected officials, our legislative process, our executive process, he added. To me it is a high-level, serious issue, and if after a couple of months you dont see any results, somebody ought to raise that to a higher level.
The F.B.I. declined to comment on the agencys handling of the hack. The F.B.I. takes very seriously any compromise of public and private sector systems, it said in a statement, adding that agents will continue to share information to help targets safeguard their systems against the actions of persistent cybercriminals.
By March, Mr. Tamene and his team had met at least twice in person with the F.B.I. and concluded that Agent Hawkins was really a federal employee. But then the situation took a dire turn.
A second team of Russian-affiliated hackers began to target the D.N.C. and other players in the political world, particularly Democrats. Billy Rinehart, a former D.N.C. regional field director who was then working for Mrs. Clintons campaign, got an odd email warning from Google.
Someone just used your password to try to sign into your Google account, the March 22 email said, adding that the sign-in attempt had occurred in Ukraine. Google stopped this sign-in attempt. You should change your password immediately.
Mr. Rinehart was in Hawaii at the time. He remembers checking his email at 4 a.m. for messages from East Coast associates. Without thinking much about the notification, he clicked on the change password button and half asleep, as best he can remember, he typed in a new password.
Photo
A screenshot of the phishing email that Billy Rinehart clicked on, unknowingly giving Russian hackers access to his account. The New York Times has redacted Mr. Rineharts email address.
What he did not know until months later is that he had just given the Russian hackers access to his email account.
Hundreds of similar phishing emails were being sent to American political targets, including an identical email sent on March 19 to Mr. Podesta, chairman of the Clinton campaign. Given how many emails Mr. Podesta received through this personal email account, several aides also had access to it, and one of them noticed the warning email, sending it to a computer technician to make sure it was legitimate before anyone clicked on the change password button.
This is a legitimate email, Charles Delavan, a Clinton campaign aide, replied to another of Mr. Podestas aides, who had noticed the alert. John needs to change his password immediately.
With another click, a decade of emails that Mr. Podesta maintained in his Gmail account a total of about 60,000 were unlocked for the Russian hackers. Mr. Delavan, in an interview, said that his bad advice was a result of a typo: He knew this was a phishing attack, as the campaign was getting dozens of them. He said he had meant to type that it was an illegitimate email, an error that he said has plagued him ever since.
Photo
Mr. Podesta, center, with Huma Abedin, Hillary Clintons closest aide, in Brooklyn the day after the election. Hackers gained access to tens of thousands of Mr. Podestas emails. Credit Dave Sanders for The New York Times
During this second wave, the hackers also gained access to the Democratic Congressional Campaign Committee, and then, through a virtual private network connection, to the main computer network of the D.N.C.
The F.B.I. observed this surge of activity as well, again reaching out to Mr. Tamene to warn him. Yet Mr. Tamene still saw no reason to be alarmed: He found copies of the phishing emails in the D.N.C.s spam filter. But he had no reason, he said, to believe that the computer systems had been infiltrated.
One bit of progress had finally been made by the middle of April: The D.N.C., seven months after it had first been warned, finally installed a robust set of monitoring tools, Mr. Tamenes internal memo says.
The United States had two decades of warning that Russias intelligence agencies were trying to break into Americas most sensitive computer networks. But the Russians have always managed to stay a step ahead.
Their first major attack was detected on Oct. 7, 1996, when a computer operator at the Colorado School of Mines discovered some nighttime computer activity he could not explain. The school had a major contract with the Navy, and the operator warned his contacts there. But as happened two decades later at the D.N.C., at first everyone was unable to connect the dots, said Thomas Rid, a scholar at Kings College in London who has studied the attack.
Investigators gave it a name Moonlight Maze and spent two years, often working day and night, tracing how it hopped from the Navy to the Department of Energy to the Air Force and NASA. In the end, they concluded that the total number of files stolen, if printed and stacked, would be taller than the Washington Monument.
Whole weapons designs were flowing out the door, and it was a first taste of what was to come: an escalating campaign of cyberattacks around the world.
But for years, the Russians stayed largely out of the headlines, thanks to the Chinese who took bigger risks, and often got caught. They stole the designs for the F-35 fighter jet, corporate secrets for rolling steel, even the blueprints for gas pipelines that supply much of the United States. And during the 2008 presidential election cycle, Chinese intelligence hacked into the campaigns of Mr. Obama and Mr. McCain, making off with internal position papers and communications. But they didnt publish any of it.
The Russians had not gone away, of course. They were just a lot more stealthy, said Kevin Mandia, a former Air Force intelligence officer who spent most of his days fighting off Russian cyberattacks before founding Mandiant, a cybersecurity firm that is now a division of FireEye and the company the Clinton campaign brought in to secure its own systems.
The Russians were also quicker to turn their attacks to political purposes. A 2007 cyberattack on Estonia, a former Soviet republic that had joined NATO, sent a message that Russia could paralyze the country without invading it. The next year cyberattacks were used during Russias war with Georgia.
But American officials did not imagine that the Russians would dare try those techniques inside the United States. They were largely focused on preventing what former Defense Secretary Leon E. Panetta warned was an approaching cyber Pearl Harbor a shutdown of the power grid or cellphone networks.
But in 2014 and 2015, a Russian hacking group began systematically targeting the State Department, the White House and the Joint Chiefs of Staff. Each time, they eventually met with some form of success, Michael Sulmeyer, a former cyberexpert for the secretary of defense, and Ben Buchanan, now both of the Harvard Cyber Security Project, wrote recently in a soon-to-be published paper for the Carnegie Endowment.
The Russians grew stealthier and stealthier, tricking government computers into sending out data while disguising the electronic command and control messages that set off alarms for anyone looking for malicious actions. The State Department was so crippled that it repeatedly closed its systems to throw out the intruders. At one point, officials traveling to Vienna with Secretary of State John Kerry for the Iran nuclear negotiations had to set up commercial Gmail accounts just to communicate with one another and with reporters traveling with them.
2016 Election Hacking Coverage
Mr. Obama was briefed regularly on all this, but he made a decision that many in the White House now regret: He did not name Russians publicly, or issue sanctions. There was always a reason: fear of escalating a cyberwar, and concern that the United States needed Russias cooperation in negotiations over Syria.
Wed have all these circular meetings, one senior State Department official said, in which everyone agreed you had to push back at the Russians and push back hard. But it didnt happen.
So the Russians escalated again breaking into systems not just for espionage, but to publish or broadcast what they found, known as doxing in the cyberworld.
It was a brazen change in tactics, moving the Russians from espionage to influence operations. In February 2014, they broadcast an intercepted phone call between Victoria Nuland, the assistant secretary of state who handles Russian affairs and has a contentious relationship with Mr. Putin, and Geoffrey Pyatt, the United States ambassador to Ukraine. Ms. Nuland was heard describing a little-known American effort to broker a deal in Ukraine, then in political turmoil.
They were not the only ones on whom the Russians used the steal-and-leak strategy. The Open Society Foundation, run by George Soros, was a major target, and when its documents were released, some turned out to have been altered to make it appear as if the foundation was financing Russian opposition members.
Last year, the attacks became more aggressive. Russia hacked a major French television station, frying critical hardware. Around Christmas, it attacked part of the power grid in Ukraine, dropping a portion of the country into darkness, killing backup generators and taking control of generators. In retrospect, it was a warning shot.
The attacks were not fully integrated military operations, Mr. Sulmeyer said. But they showed an increasing boldness.
Cozy Bear and Fancy Bear
The day before the White House Correspondents Association dinner in April, Ms. Dacey, the D.N.C.s chief executive, was preparing for a night of parties when she got an urgent phone call.
With the new monitoring system in place, Mr. Tamene had examined administrative logs of the D.N.C.s computer system and found something very suspicious: An unauthorized person, with administrator-level security status, had gained access to the D.N.C.s computers.
Not sure it is related to what the F.B.I. has been noticing, said one internal D.N.C. email sent on April 29. The D.N.C. may have been hacked in a serious way this week, with password theft, etc.
An American counterstrike
has got to be overt.
It needs to be seen.
MICHAEL MORELL, former deputy director of the C.I.A.
No one knew just how bad the breach was but it was clear that a lot more than a single filing cabinet worth of materials might have been taken. A secret committee was immediately created, including Ms. Dacey, Ms. Wasserman Schultz, Mr. Brown and Michael Sussmann, a former cybercrimes prosecutor at the Department of Justice who now works at Perkins Coie, the Washington law firm that handles D.N.C. political matters.
Three most important questions, Mr. Sussmann wrote to his clients the night the break-in was confirmed. 1) What data was accessed? 2) How was it done? 3) How do we stop it?
Mr. Sussmann instructed his clients not to use D.N.C. email because they had just one opportunity to lock the hackers out an effort that could be foiled if the hackers knew that the D.N.C. was on to them.
You only get one chance to raise the drawbridge, Mr. Sussmann said. If the adversaries know you are aware of their presence, they will take steps to burrow in, or erase the logs that show they were present.
Photo
Michael Sussmann, a Washington lawyer and former cybercrime prosecutor at the Justice Department, received an email in late April confirming that the D.N.C.s computer system had been compromised.
The D.N.C. immediately hired CrowdStrike, a cybersecurity firm, to scan its computers, identify the intruders and build a new computer and telephone system from scratch. Within a day, CrowdStrike confirmed that the intrusion had originated in Russia, Mr. Sussmann said.
The work that such companies do is a computer version of old-fashioned crime scene investigation, with fingerprints, bullet casings and DNA swabs replaced by an electronic trail that can be just as incriminating. And just as police detectives learn to identify the telltale methods of a veteran burglar, so CrowdStrike investigators recognized the distinctive handiwork of Cozy Bear and Fancy Bear.
Those are CrowdStrikes nicknames for the two Russian hacking groups that the firm found at work inside the D.N.C. network. Cozy Bear the group also known as the Dukes or A.P.T. 29, for advanced persistent threat may or may not be associated with the F.S.B., the main successor to the Soviet-era K.G.B., but it is widely believed to be a Russian government operation. It made its first appearance in 2014, said Dmitri Alperovitch, CrowdStrikes co-founder and chief technology officer.
It was Cozy Bear, CrowdStrike concluded, that first penetrated the D.N.C. in the summer of 2015, by sending spear-phishing emails to a long list of American government agencies, Washington nonprofits and government contractors. Whenever someone clicked on a phishing message, the Russians would enter the network, exfiltrate documents of interest and stockpile them for intelligence purposes.
Once they got into the D.N.C., they found the data valuable and decided to continue the operation, said Mr. Alperovitch, who was born in Russia and moved to the United States as a teenager.
Only in March 2016 did Fancy Bear show up first penetrating the computers of the Democratic Congressional Campaign Committee, and then jumping to the D.N.C., investigators believe. Fancy Bear, sometimes called A.P.T. 28 and believed to be directed by the G.R.U., Russias military intelligence agency, is an older outfit, tracked by Western investigators for nearly a decade. It was Fancy Bear that got hold of Mr. Podestas email.
Attribution, as the skill of identifying a cyberattacker is known, is more art than science. It is often impossible to name an attacker with absolute certainty. But over time, by accumulating a reference library of hacking techniques and targets, it is possible to spot repeat offenders. Fancy Bear, for instance, has gone after military and political targets in Ukraine and Georgia, and at NATO installations.
That largely rules out cybercriminals and most countries, Mr. Alperovitch said. Theres no plausible actor that has an interest in all those victims other than Russia, he said. Another clue: The Russian hacking groups tended to be active during working hours in the Moscow time zone.
To their astonishment, Mr. Alperovitch said, CrowdStrike experts found signs that the two Russian hacking groups had not coordinated their attacks. Fancy Bear, apparently not knowing that Cozy Bear had been rummaging in D.N.C. files for months, took many of the same documents.
In the six weeks after CrowdStrikes arrival, in total secrecy, the computer system at the D.N.C. was replaced. For a weekend, email and phones were shut off; employees were told it was a system upgrade. All laptops were turned in and the hard drives wiped clean, with the uninfected information on them imaged to new drives.
Though D.N.C. officials had learned that the Democratic Congressional Campaign Committee had been infected, too, they did not notify their sister organization, which was in the same building, because they were afraid that it would leak.
All of this work took place as the bitter contest for the Democratic nomination continued to play out between Mrs. Clinton and Mr. Sanders, and it was already causing a major distraction for Ms. Wasserman Schultz and the D.N.C.s chief executive.
This was not a bump in the road bumps in the road happen all the time, she said in an interview. Two different Russian spy agencies had hacked into our network and stolen our property. And we did not yet know what they had taken. But we knew they had very broad access to our network. There was a tremendous amount of uncertainty. And it was chilling.
The D.N.C. executives and their lawyer had their first formal meeting with senior F.B.I. officials in mid-June, nine months after the bureaus first call to the tech-support contractor. Among the early requests at that meeting, according to participants: that the federal government make a quick attribution formally blaming actors with ties to Russian government for the attack to make clear that it was not routine hacking but foreign espionage.
You have a presidential election underway here and you know that the Russians have hacked into the D.N.C., Mr. Sussmann said, recalling the message to the F.B.I. We need to tell the American public that. And soon.
The Medias Role
In mid-June, on Mr. Sussmanns advice, D.N.C. leaders decided to take a bold step. Concerned that word of the hacking might leak, they decided to go public in The Washington Post with the news that the committee had been attacked. That way, they figured, they could get ahead of the story, win a little sympathy from voters for being victimized by Russian hackers and refocus on the campaign.
But the very next day, a new, deeply unsettling shock awaited them. Someone calling himself Guccifer 2.0 appeared on the web, claiming to be the D.N.C. hacker and he posted a confidential committee document detailing Mr. Trumps record and half a dozen other documents to prove his bona fides.
And its just a tiny part of all docs I downloaded from the Democrats networks, he wrote. Then something more ominous: The main part of the papers, thousands of files and mails, I gave to WikiLeaks. They will publish them soon.
It was bad enough that Russian hackers had been spying inside the committees network for months. Now the public release of documents had turned a conventional espionage operation into something far more menacing: political sabotage, an unpredictable, uncontrollable menace for Democratic campaigns.
Guccifer 2.0 borrowed the moniker of an earlier hacker, a Romanian who called himself Guccifer and was jailed for breaking into the personal computers of former President George W. Bush, former Secretary of State Colin L. Powell and other notables. This new attacker seemed intent on showing that the D.N.C.s cyberexperts at CrowdStrike were wrong to blame Russia. Guccifer 2.0 called himself a lone hacker and mocked CrowdStrike for calling the attackers sophisticated.
But online investigators quickly undercut his story. On a whim, Lorenzo Franceschi-Bicchierai, a writer for Motherboard, the tech and culture site of Vice, tried to contact Guccifer 2.0 by direct message on Twitter.
Surprisingly, he answered right away, Mr. Franceschi-Bicchierai said. But whoever was on the other end seemed to be mocking him. I asked him why he did it, and he said he wanted to expose the Illuminati. He called himself a Gucci lover. And he said he was Romanian.
That gave Mr. Franceschi-Bicchierai an idea. Using Google Translate, he sent the purported hacker some questions in Romanian. The answers came back in Romanian. But when he was offline, Mr. Franceschi-Bicchierai checked with a couple of native speakers, who told him Guccifer 2.0 had apparently been using Google Translate as well and was clearly not the Romanian he claimed to be.
Cyberresearchers found other clues pointing to Russia. Microsoft Word documents posted by Guccifer 2.0 had been edited by someone calling himself, in Russian, Felix Edmundovich an obvious nom de guerre honoring the founder of the Soviet secret police, Felix Edmundovich Dzerzhinsky. Bad links in the texts were marked by warnings in Russian, generated by what was clearly a Russian-language version of Word.
When Mr. Franceschi-Bicchierai managed to engage Guccifer 2.0 over a period of weeks, he found that his interlocutors tone and manner changed. At first he was careless and colloquial. Weeks later, he was curt and more calculating, he said. It seemed like a group of people, and a very sloppy attempt to cover up.
Computer experts drew the same conclusion about DCLeaks.com, a site that sprang up in June, claiming to be the work of hacktivists but posting more stolen documents. It, too, seemed to be a clumsy front for the same Russians who had stolen the documents. Notably, the website was registered in April, suggesting that the Russian hacking team planned well in advance to make public what it stole.
In addition to what Guccifer 2.0 published on his site, he provided material directly on request to some bloggers and publications. The steady flow of Guccifer 2.0 documents constantly undercut Democratic messaging efforts. On July 6, 12 days before the Republican National Convention began in Cleveland, Guccifer released the D.N.C.s battle plan and budget for countering it. For Republican operatives, it was insider gold.
Then WikiLeaks, a far more established outlet, began to publish the hacked material just as Guccifer 2.0 had promised. On July 22, three days before the start of the Democratic National Convention in Philadelphia, WikiLeaks dumped out 44,053 D.N.C. emails with 17,761 attachments. Some of the messages made clear that some D.N.C. officials favored Mrs. Clinton over her progressive challenger, Mr. Sanders.
That was no shock; Mr. Sanders, after all, had been an independent socialist, not a Democrat, during his long career in Congress, while Mrs. Clinton had been one of the partys stars for decades. But the emails, some of them crude or insulting, infuriated Sanders delegates as they arrived in Philadelphia. Ms. Wasserman Schultz resigned under pressure on the eve of the convention where she had planned to preside.
Mr. Trump, by now the Republican nominee, expressed delight at the continuing jolts to his opponent, and he began to use Twitter and his stump speeches to highlight the WikiLeaks releases. On July 25, he sent out a lighthearted tweet: The new joke in town, he wrote, is that Russia leaked the disastrous D.N.C. e-mails, which should never have been written (stupid), because Putin likes me.
But WikiLeaks was far from finished. On Oct. 7, a month before the election, the site began the serial publication of thousands of private emails to and from Mr. Podesta, Mrs. Clintons campaign manager.
The same day, the United States formally accused the Russian government of being behind the hackings, in a joint statement by the director of national intelligence and the Department of Homeland Security, and Mr. Trump suffered his worst blow to date, with the release of a recording in which he bragged about sexually assaulting women.
The Podesta emails were nowhere near as sensational as the Trump video. But, released by WikiLeaks day after day over the last month of the campaign, they provided material for countless news reports. They disclosed the contents of Mrs. Clintons speeches to large banks, which she had refused to release. They exposed tensions inside the campaign, including disagreements over donations to the Clinton Foundation that staff members thought might look bad for the candidate and Ms. Tandens complaint that Mrs. Clintons instincts were suboptimal.
I was just mortified, Ms. Tanden said in an interview. Her emails were released on the eve of one of the presidential debates, she recalled. I put my hands over my head and said, I cant believe this is happening to me. Though she had regularly appeared on television to support Mrs. Clinton, she canceled her appearances because all the questions were about what she had said in the emails.
Ms. Tanden, like other Democrats whose messages became public, said it was obvious to her that WikiLeaks was trying its best to damage the Clinton campaign. If you care about transparency, you put all the emails out at once, she said. But they wanted to hurt her. So they put them out 1,800 to 3,000 a day.
The Trump campaign knew in advance about WikiLeaks plans. Days before the Podesta email release began, Roger Stone, a Republican operative working with the Trump campaign, sent out an excited tweet about what was coming.
But in an interview, Mr. Stone said he had no role in the leaks; he had just heard from an American with ties to WikiLeaks that damning emails were coming.
Julian Assange, the WikiLeaks founder and editor, has resisted the conclusion that his site became a pass-through for Russian hackers working for Mr. Putins government or that he was deliberately trying to undermine Mrs. Clintons candidacy. But the evidence on both counts appears compelling.
In a series of email exchanges, Mr. Assange refused to say anything about WikiLeaks source for the hacked material. He denied that he had made his animus toward Mrs. Clinton clear in public statements (False. But what is this? Junior high?) or that the site had timed the releases for maximum negative effect on her campaign. WikiLeaks makes its decisions based on newsworthiness, including for its recent epic scoops, he wrote.
Mr. Assange disputed the conclusion of the Oct. 7 statement from the intelligence agencies that the leaks were intended to interfere with the U.S. election process.
This is false, he wrote. As the disclosing party we know that this was not the intent. Publishers publishing newsworthy information during an election is part of a free election.
But asked whether he believed the leaks were one reason for Mr. Trumps election, Mr. Assange seemed happy to take credit. Americans extensively engaged with our publications, he wrote. According to Facebook statistics WikiLeaks was the most referenced political topic during October.
Though Mr. Assange did not say so, WikiLeaks best defense may be the conduct of the mainstream American media. Every major publication, including The Times, published multiple stories citing the D.N.C. and Podesta emails posted by WikiLeaks, becoming a de facto instrument of Russian intelligence.
Mr. Putin, a student of martial arts, had turned two institutions at the core of American democracy political campaigns and independent media to his own ends. The medias appetite for the hacked material, and its focus on the gossipy content instead of the Russian source, disturbed some of those whose personal emails were being reposted across the web.
What was really surprising to me? Ms. Tanden said. I could not believe that reporters were covering it.
Inside the White House, as Mr. Obamas advisers debated their response, their conversation turned to North Korea.
In late 2014, hackers working for Kim Jong-un, the Norths young and unpredictable leader, had carried out a well-planned attack on Sony Pictures Entertainment intended to stop the Christmastime release of a comedy about a C.I.A. plot to kill Mr. Kim.
In that case, embarrassing emails had also been released. But the real damage was done to Sonys own systems: More than 70 percent of its computers melted down when a particularly virulent form of malware was released. Within weeks, intelligence agencies traced the attack back to the North and its leadership. Mr. Obama called North Korea out in public, and issued some not-very-effective sanctions. The Chinese even cooperated, briefly cutting off the Norths internet connections.
As the first Situation Room meetings on the Russian hacking began in July, it was clear that Russia was going to be a much more complicated case, said one participant. The Russians clearly had a more sophisticated understanding of American politics, and they were masters of kompromat, their term for compromising information.
But a formal attribution report still had not been forwarded to the president.
It took forever, one senior administration official said, complaining about the pace at which the intelligence assessments moved through the system.
In August a group that called itself the Shadow Brokers published a set of software tools that looked like what the N.S.A. uses to break into foreign computer networks and install implants, malware that can be used for surveillance or attack. The code came from the Tailored Access Operations unit of the N.S.A., a secretive group that mastered the arts of surveillance and cyberwar.
The assumption still unproved was that the code was put out in the open by the Russians as a warning: Retaliate for the D.N.C., and there are a lot more secrets, from the hackings of the State Department, the White House and the Pentagon, that might be spilled as well. One senior official compared it to the scene in The Godfather where the head of a favorite horse is left in a bed, as a warning.
The N.S.A. said nothing. But by late August, Admiral Rogers, its director, was pressing for a more muscular response to the Russians. In his role as director of the Pentagons Cyber Command, he proposed a series of potential counter-cyberstrikes.
While officials will not discuss them in detail, the possible counterstrikes reportedly included operations that would turn the tables on Mr. Putin, exposing his financial links to Russias oligarchs, and punching holes in the Russian internet to allow dissidents to get their message out. Pentagon officials judged the measures too unsubtle and ordered up their own set of options.
But in the end, none of those were formally presented to the president.
In a series of deputies meetings run by Avril Haines, the deputy national security adviser and a former deputy director of the C.I.A., several officials warned that an overreaction by the administration would play into Mr. Putins hands.
If we went to Defcon 4, one frequent participant in Ms. Hainess meetings said, using a phrase from the Cold War days of warnings of war, we would be saying to the public that we didnt have confidence in the integrity of our voting system.
Even something seemingly straightforward using the presidents executive powers, bolstered after the Sony incident, to place economic and travel sanctions on cyberattackers seemed too risky.
No one was all that eager to impose costs before Election Day, said another participant in the classified meeting. Any retaliatory measures were seen through the prism of what would happen on Election Day.
Instead, when Mr. Obamas national security team reconvened after summer vacation, the focus turned to a crash effort to secure the nations voting machines and voter-registration rolls from hacking. The scenario they discussed most frequently one that turned out not to be an issue was a narrow vote in favor of Mrs. Clinton, followed by a declaration by Mr. Trump that the vote was rigged and more leaks intended to undercut her legitimacy.
Donna Brazile, the interim chairwoman of the D.N.C., became increasingly frustrated as the clock continued to run down on the presidential election and still there was no broad public condemnation by the White House, or Republican Party leaders, of the attack as an act of foreign espionage.
Ms. Brazile even reached out to Reince Priebus, the chairman of the Republican National Committee, urging him twice in private conversations and in a letter to join her in condemning the attacks an offer he declined to take up.
We just kept hearing the government would respond, the government would respond, she said. Once upon a time, if a foreign government interfered with our election we would respond as a nation, not as a political party.
Got a confidential news tip?
But Mr. Obama did decide that he would deliver a warning to Mr. Putin in person at a Group of 20 summit meeting in Hangzhou, China, the last time they would be in the same place while Mr. Obama was still in office. When the two men met for a tense pull-aside, Mr. Obama explicitly warned Mr. Putin of a strong American response if there was continued effort to influence the election or manipulate the vote, according to White House officials who were not present for the one-on-one meeting.
Later that day, Mr. Obama made a rare reference to Americas own offensive cybercapacity, which he has almost never talked about. Frankly, both offensively and defensively, we have more capacity, he told reporters.
But when it came time to make a public assertion of Russias role in early October, it was made in a written statement from the director of national intelligence and the secretary of homeland security. It was far less dramatic than the presidents appearance in the press room two years before to directly accuse the North Koreans of attacking Sony.
The reference in the statement to hackings on political organizations, officials now say, encompassed a hacking on data stored by the Republicans as well. Two senior officials say the forensic evidence was accompanied by human and technical sources in Russia, which appears to mean that the United States implants or taps in Russian computer and phone networks helped confirm the countrys role.
But that may not be known for decades, until the secrets are declassified.
A week later Vice President Joseph R. Biden Jr. was sent out to transmit a public warning to Mr. Putin: The United States will retaliate at the time of our choosing. And under the circumstances that have the greatest impact.
Later, after Mr. Biden said he was not concerned that Russia could fundamentally alter the election, he was asked whether the American public would know if the message to Mr. Putin had been sent.
Hope not, Mr. Biden responded.
Some of his former colleagues think that was the wrong answer. An American counterstrike, said Michael Morell, the former deputy director of the C.I.A. under Mr. Obama, has got to be overt. It needs to be seen.
A covert response would significantly limit the deterrence effect, he added. If you cant see it, its not going to deter the Chinese and North Koreans and Iranians and others.
The Obama administration says it still has more than 30 days to do exactly that.
As the year draws to a close, it now seems possible that there will be multiple investigations of the Russian hacking the intelligence review Mr. Obama has ordered completed by Jan. 20, the day he leaves office, and one or more congressional inquiries. They will wrestle with, among other things, Mr. Putins motive.
Did he seek to mar the brand of American democracy, to forestall anti-Russian activism for both Russians and their neighbors? Or to weaken the next American president, since presumably Mr. Putin had no reason to doubt American forecasts that Mrs. Clinton would win easily? Or was it, as the C.I.A. concluded last month, a deliberate attempt to elect Mr. Trump?
In fact, the Russian hack-and-dox scheme accomplished all three goals.
What seems clear is that Russian hacking, given its success, is not going to stop. Two weeks ago, the German intelligence chief, Bruno Kahl, warned that Russia might target elections in Germany next year. The perpetrators have an interest to delegitimize the democratic process as such, Mr. Kahl said. Now, he added, Europe is in the focus of these attempts of disturbance, and Germany to a particularly great extent.
But Russia has by no means forgotten its American target. On the day after the presidential election, the cybersecurity company Volexity reported five new waves of phishing emails, evidently from Cozy Bear, aimed at think tanks and nonprofits in the United States.
One of them purported to be from Harvard University, attaching a fake paper. Its title: Why American Elections Are Flawed.
Correction: December 13, 2016
Kitty Bennett contributed research. |
|
|
 Fri Dec 30, 2016 7:04 am
Fri Dec 30, 2016 7:04 am |
|
|
untanglingwebs
El Supremo
|
USA TODAY
Russia penetrated Vermont utility company computer
April McCullum and Elizabeth Weise, USA TODAY Network 12:10 a.m. EST December 31, 2016
123016burlington-electric2.jpg
(Photo: Aki Soga, The Burlington (Vt.) Free Press)
BURLINGTON, Vt. Malicious software believed tied to a Russian hacking group associated with attempts to influence the U.S. presidential election was found Friday within a computer that belongs to Burlington Electric, one of Vermonts electrical utilities.
The utility found the malware on a laptop not connected to the operation of the grid, said Commissioner Christopher Recchia of Vermont's Public Service Department.
Based on his knowledge, Recchia said Friday night he did not believe that the electrical power grid was at risk from the incident.
Could hackers knock out our power? It happened in Ukraine
"The grid is not in danger," Recchia said. "The utility flagged it, saw it, notified appropriate parties and isolated that one laptop with that malware on it."
Attacks on the nation's electrical grid are among several infrastructure attack scenarios that worry officials and cyber-security experts. Critical infrastructure systems are often run on older computer networks and often difficult to protect.
The grid is not in danger. The utility flagged it, saw it, notified appropriate parties and isolated that one laptop with that malware on it.
Christopher Recchia, Vermont Public Service Department
Ukraine has accused Russia of hacking into its electrical utilities and turning off power to several regions.
The Obama administration released code associated with the Russian hacking group, dubbed Grizzly Steppe, on Thursday.
The aim of the release was to allow utilities, companies and organizations to search their computers for the digital signatures of the attack code, to see if they, too, had been targeted.
That proved to be a good strategy with the announcement Friday evening that the code had been found in the city-owned system in Vermont. Another Vermont utility, Vermont Electric Cooperative based in Johnson, Vt., said it found no evidence of a threat to its system.
Vermont officials, all Democrats, weighed in on the announcement:
Gov. Peter Shumlin: "This episode should highlight the urgent need for our federal government to vigorously pursue and put an end to this sort of Russian meddling." His statement also called Russian President Vladimir Putin a thug.
Sen. Patrick Leahy: "State-sponsored Russian hacking is a serious threat, and the attempts to penetrate the electric grid through a Vermont utility are the latest example. ... This is now about trying to access utilities to potentially manipulate the grid and shut it down in the middle of winter."
Rep. Peter Welch: "This attack shows how rampant Russian hacking is. It's systemic, relentless, predatory."
It is unclear whether the penetration in Burlington was an attempt to disrupt the utility or simply a test.
"We acted quickly to scan all computers in our system for the malware signature. We detected the malware in a single Burlington Electric Department laptop not connected to our organizations grid systems. We took immediate action to isolate the laptop and alerted federal officials of this finding," Mike Kanarick, spokesman for the Burlington Electric Department, said in a statement.
Sanctions mark rare window into cyberwar
The utility is working with federal officials to trace the malware and prevent any other attempts to infiltrate utility systems. It also has briefed state officials.
"As commissioner of public service we are very concerned about cybersecurity," Recchia said. "I've been working with Homeland Security and our Department of Emergency Management's Homeland Security to make sure that we are on top of things like this because this is a real concern."
April McCullum reports for The Burlington (Vt.) Free Press; Elizabeth Weise reports for USA TODAY from San Francisco. Follow them on Twitter: @april_mccullum and @eweise
Water flows through the Winooski 1 hydro-electric plant
Water flows through the Winooski 1 hydro-electric plant in Winooski, Vt., on Sept. 10, 2014. The Burlington Electric Department's recent purchase of the facility, located in the Winooski River between Burlington and the city of Winooski, enabled it to reach 100% renewable power. (Ph |
|
|
 Sat Dec 31, 2016 6:29 am
Sat Dec 31, 2016 6:29 am |
|
|
untanglingwebs
El Supremo
|
The DHS and FBI also publicly posted information about the malware Thursday as part of a joint analysis report, saying that the Russian military and civilian services activity is part of an ongoing campaign of cyber-enabled operations directed at the U.S. government and its citizens.
Another senior administration official, who also spoke on the condition of anonymity to discuss security matters, said in an email that by exposing Russian malware in the joint analysis report, the administration sought to alert all network defenders in the United States and abroad to this malicious activity to better secure their networks and defend against Russian malicious cyber activity.
According to the report by the FBI and DHS, the hackers involved in the Russian operation used fraudulent emails that tricked their recipients into revealing passwords.
Official Copy: https://www.us-cert.gov/
/JAR_16-20296A_GRIZZLY%20STEPPE-20
This Joint Analysis Report (JAR) is the result of analytic efforts between the Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI). This document
provides technical details regarding the tools and infrastructure used by the Russian civilian and military intelligence Services (RIS) to compromise and exploit networks and endpoints
associated with the U.S. election, as well as a range of U.S.
Government, political, and private sector entities.
The U.S. Government is referring to this malicious cyber
activity by RIS as GRIZZLY STEPPE. |
|
|
 Sat Dec 31, 2016 9:06 am
Sat Dec 31, 2016 9:06 am |
|
|
|
 FlintTalk.com Forum Index
> Political Talk
FlintTalk.com Forum Index
> Political Talk